1. Introduction
A vital function of contemporary computer networks is the Network Time Protocol (NTP). NTP keeps clocks synchronized across devices. Despite being necessary, NTP is susceptible to security risks.
In this tutorial, we’ll discuss security issues and how authentication techniques improve time synchronization’s dependability and integrity.
2. What Is NTP?
Network Time Protocol (NTP) synchronizes computer clocks across a network. It guarantees that the precise time of every device on the network is the same.
The NTP protocol modifies the client’s clock by exchanging time signals with the server. Network operations often need to synchronize tasks, protect data, and maintain the correct order of events.
In essence, NTP keeps a computer network operating efficiently and punctually. Accurate timestamps facilitate compliance, forensic investigation, and troubleshooting.
Additionally, accurate timing facilitates incident detection and response. For safe communication, authentication systems depend on a common temporal reference.
Toll plaza systems, for example, ensure accurate billing by keeping the clocks synchronized.
3. What Are the Features of NTP?
The following table shows the features of NTP:
Feature
Description
Reference clock
For all synchronization activities, NTP offers a reference clock that serves as a source of reference
Synchronization protocol
Automatically looks for the best time sources. In addition, any network node can transmit time information bidirectionally (point-to-point) or uni-directionally (one direction)
Scalable
Easily scales to accommodate a large number of subscribers without significantly increasing the load on the server or the network
Efficiency
Need less bandwidth for synchronization in a complex network using multicast
Redundancy
Accurate timekeeping can continue even if one peer loses its connection to an external time source by using the other peer to synchronize its clock
4. What Are the Modes of NTP Operation?
The four modes of operation for NTP are Client/Server, Symmetric (Peer), Broadcast and Multicast.
4.1. Client/Server Mode
In this mode, both the client and the server have their clocks. The following sequence diagram illustrates the exchange of messages between the client and the server:
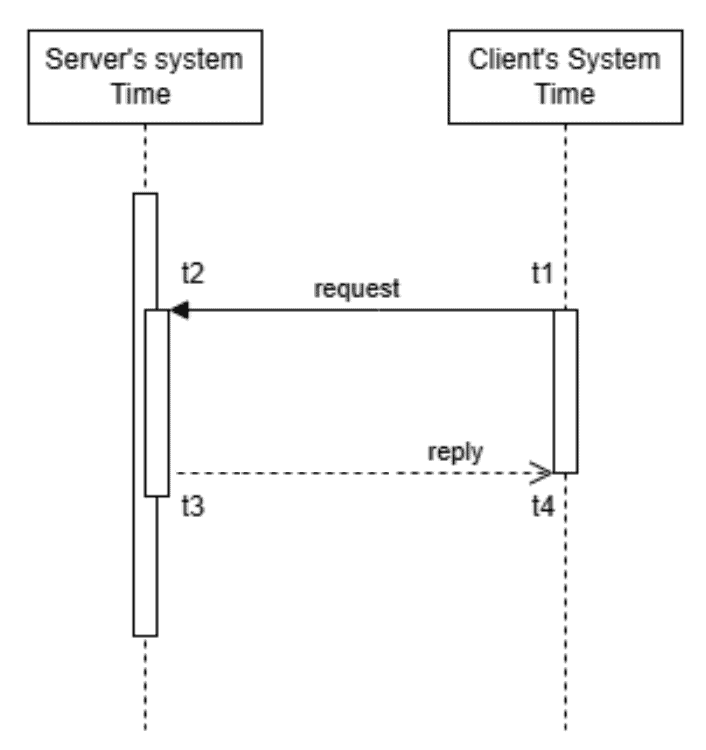
After submitting an NTP request to the server, the client logs the message’s transmission time (t1). Following this, the server records the message’s arrival time at the server (t2), processes the request (t3), and replies to the client.
Further, after receiving the server’s response, the client records the time of its arrival (t4). The NTP procedure assists the client in modifying its clock to correspond with the server’s time during synchronization.
The NTP message’s round-trip delay is (t4-t1) – (t3-t2).
The time difference between the client and server is ((t2-t1) + (t3-t4))/ 2. This time difference aids in synchronizing the client’s clock with the server’s time.
Further, a single synchronization attempt may not suffice due to the inherent uncertainties and variations in network transmission times. Multiple synchronizations might be needed to get a good result.
4.2. Security and Authentication in NTP
NTP frequently makes use of several servers to improve accuracy and dependability. Clients can compare time data from various servers and identify discrepancies. Another important component of protecting the system from malevolent servers is this redundancy.
A feature known as Byzantine Fault Tolerance (BFT) enables the system to keep operating properly even if some of its parts malfunction or behave maliciously.
Regarding synchronization and NTP two key aspects are:
- Byzantine faults: These happen when parts of a distributed system behave erratically or give contradicting information because of malicious attacks, or hardware and software malfunctions.
- BFT in NTP: The NTP provides dependable time synchronization even in the event of Byzantine faults. This guarantees that the system can still converge at an accurate time even if some servers are malicious.
Clients can determine the most popular time by utilizing replies from several servers. If a server’s response deviates greatly from the majority, it can be identified as potentially malicious.
Additionally, we can protect time synchronization infrastructure from malicious threats by putting strong authentication procedures in place, and adhering to security best practices.
By taking care of these points, the network’s overall security posture is strengthened and NTP’s dependability is increased.
4.3. Symmetric (Peer) Mode
In this mode, two servers act as peers, exchanging time information to synchronize. Both devices send and receive updates, providing redundancy and improving accuracy, as shown below:
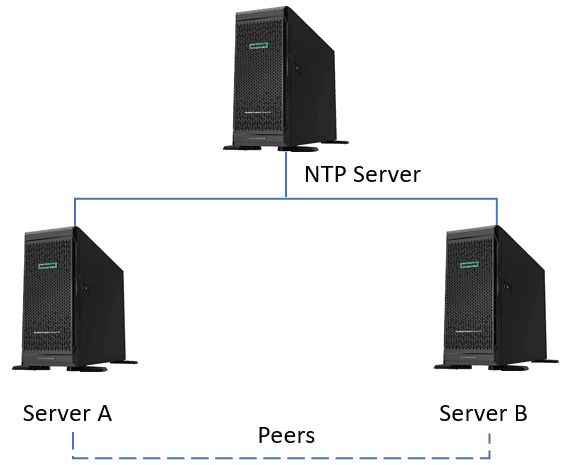
The NTP server’s local clock is a reference source. Server A will work in client mode, using the NTP server as the server. Server B will work in symmetric-active mode, with server A as its peer.
The communication process between peer server A and the NTP server follows the same steps as described in section 4.1.
Further, the communication between peer servers A and B (in the absence of the NTP server) also follows the same procedure.
This model is reliable timekeeping in critical systems like data centers and financial networks. It ensures that even if one source of time becomes unavailable, the system can continue to function correctly using the time data from the remaining peers.
4.4. Broadcast Mode
Let’s discuss broadcast mode. The NTP server uses a broadcast address to provide time updates to several clients at once. Broadcast eliminates the need for individual requests for time updates and allows all clients on the same network segment to receive them.
This mode is ideal for local area networks (LANs) that allow for broadcast transmission and minimize the number of individual requests, which lessens the stress on the network and server.
Because it lowers overall network traffic, this technique works well for big networks.
4.5. Multicast Mode
An NTP server transmits time updates to a designated multicast group address in multicast mode.
This mode can be helpful for clients who are dispersed among several network segments but still require synchronized time.
This mode is ideal for more complicated and sizable networks where broadcasting might not be practical. Further, this mode uses multicast addressing to assist in reducing network congestion.
For example, IPTV (Internet Protocol Television) services have several internet service providers for television programs. They can use multicast for their user’s devices via a network.
5. What Are the Security Challenges in NTP?
Sometimes, NTP exposes systems to attacks that might alter time synchronization, endangering the security and integrity of the network. Furthermore, the unauthorized time servers altering the time data could result in inconsistencies and weaknesses in network operations.
Further, if attackers manage to mess with time synchronization, it could seriously harm the integrity and security of many systems as follows:
Attacks
Impact
Spoofing
Malicious actors forging NTP packets could interfere with time synchronization or change system behavior
Man-in-the-Middle (MitM)
Before the time information reaches the intended receiver, an attacker can alter it by intercepting NTP data. This may result in imprecise timekeeping and possible security lapses.
When an NTP server receives too many queries, it may not function normally, which could interfere with genuine clients’ ability to synchronize their time
The above table shows why focusing on NTP security and verification is crucial.
6. Authentication in NTP
NTP authentication is essential to ensure the precision and safety of time synchronization across networked devices.
NTP authentication methods usually use cryptographic techniques to confirm the authenticity of time servers. The NTP ensures that the time data has not been tampered with during transmission.
Additionally, NTP can offer strong authentication by using cryptographic techniques like digital signatures and symmetric key algorithms, protecting the dependability and integrity of time synchronization.
Authentication is crucial for stopping attacks and preserving a network’s security and functionality:
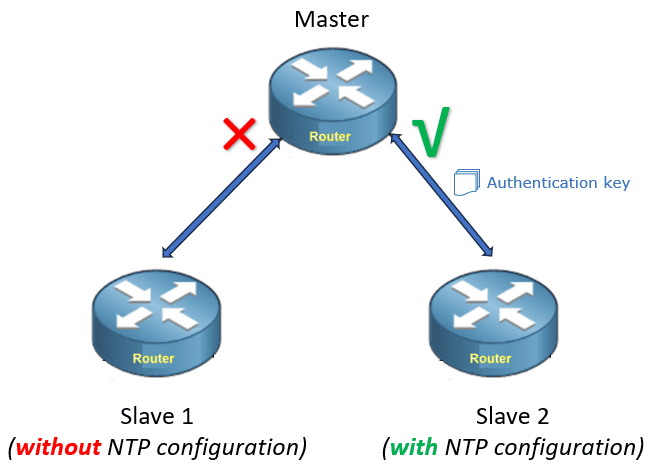
A master is a router and has a standard time set-up. Let’s assume the master is a NTP server and slaves 1 and 2 are NTP clients. To make slaves 1 and 2 sync up time from the master securely, we’ll need to set up authentication on NTP.
As shown in the figure, slave 1 is without NTP configuration and doesn’t have an authentication key to sync up with the master.
Furthermore, slave 2 has an NTP configuration and has an authentication key to sync up with the master.
7. What Are the Best Practices?
Adhering to established practices can save us from trouble when dealing with NTP synchronization failures.
To guard against MitM and spoofing attacks, we’ll use authentication methods such as PKI or symmetric keys. Further, we’ll use firewalls and access control lists to grant only authorized clients access to NTP servers.
NTP software and configurations should be current with the most recent security patches and enhancements.
Monitor for unusual traffic patterns or high mistake rates, among other suspicious activity. Finally, to safeguard NTP servers and clients from intrusions and assaults, need to enforce robust security standards.
8. Conclusion
In this article, we explored security concerns and how authentication methods enhance the reliability and integrity of time synchronization.
Network security, industrial control systems, and financial transactions are just a few of the vital systems that depend on secure NTP. Organizations may maintain precise and safe timekeeping throughout their networks by following best practices and keeping up with the most recent security developments.