1. Overview
Data security is a top priority in today’s digital landscape. Strategies to protect sensitive information have evolved to address the ever-growing threats. To counteract these risks, organizations employ various methods and tools to safeguard devices and communications.
For comprehensive coverage, organizations use data loss prevention software, which monitors data flows and enforces security policies based on data classification. Additionally, having a response plan in the event of breaches can mitigate the impact.
In this tutorial, let’s discuss what is DLP and its best practices.
2. What Is DLP?
Data Loss Prevention (DLP) is a set of strategies, tools, and practices designed to prevent the unauthorized access, sharing, or loss of sensitive data. DLP ensures that confidential data, personal and financial statements, intellectual property, or any other type of sensitive information remains protected throughout its lifecycle.
The core function of DLP is to detect and prevent data breaches by monitoring, identifying, and responding to potential risks. It also ensures that sensitive data is not improperly accessed or transferred by unauthorized individuals, systems, or applications. DLP enforces security policies that control how we manage, share, and store data within an organization. These policies should meet regulatory requirements like GDPR, HIPAA, or CCPA and address specific industry risks.
As organizations increasingly rely on digital information, safeguarding this data from accidental and malicious threats is critical.
2.1. How DLP Works?
For DLP to work effectively, we define policies that dictate how we handle sensitive data. As mentioned before, these policies should align with regulatory requirements and the organization’s security objectives.
Additionally, the policies should cover the different types of sensitive information.
Following, we implement DLP tools that monitor data in three key states: at rest, in motion, and in use:
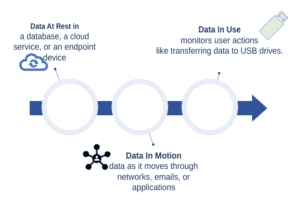
When data is at rest, it’s stored in a database, a cloud service, or an endpoint device. A DLP system scans and classifies data based on predefined rules. We can then apply encryption, access controls, and other measures to ensure authorized personnel can view or manipulate the data.
For data in motion, DLP monitors data as it moves through networks, emails, or applications. It inspects the content, looking for patterns such as credit card numbers or proprietary information. A policy violation occurs if someone attempts to send sensitive information to an external email, and DLP blocks or quarantines the action.
When data in use, DLP monitors user actions to detect unusual behavior. We can then enforce policies like restricting copy-pasting, printing, or transferring data to USB drives.
When implementing these techniques, DLP helps us protect sensitive information, as we remain compliant with data security regulations.
Also, we can configure the system to generate alerts and reports, allowing us to respond quickly to any potential data breaches or misuse.
2.2. Types of DLP
We categorize Data Loss Prevention (DLP) into three main types: endpoint, network, and storage. Each type plays a crucial role in safeguarding sensitive data:
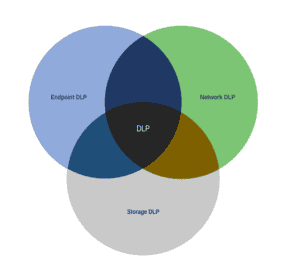
Firstly, we’ll look at endpoint DLP, which protects data directly on a user’s device, such as laptops or desktops. This solution involves deploying agents that monitor activities like file transfers and data access. When it detects an attempt to share sensitive information through unauthorized channels, the system can block that action or alert us. By controlling data at the endpoint, we prevent leaks before they occur.
Following this, we use network DLP to oversee data in transit. It examines network traffic, ensuring that sensitive information does not leave our organization without permission. When data moves through email, web applications, or cloud services, we utilize content inspection techniques to identify and classify sensitive data. If we detect a potential breach, network DLP can either block the transmission or notify our security team, thus reducing the risk of data exfiltration.
Lastly, we use storage DLP to manage data at rest. It involves scanning databases, file systems, and cloud storage for sensitive information. We enforce strict access controls and encryption by classifying and tagging data according to its sensitivity. Whenever we identify unprotected sensitive data, we can take action to secure it and ensure compliance with our data protection policies.
All these types of DLP are to address specific vulnerabilities. Endpoint DLP safeguards user devices, network DLP safeguards data in transit, and storage DLP safeguards data in storage. Together, these solutions create a robust defense against data loss, helping us maintain compliance and protect our most valuable information.
3. Potential Risks in Data Handling
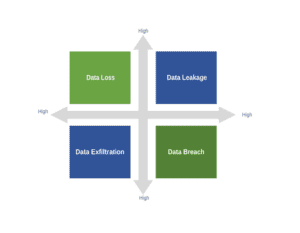
Let’s look at how we can use DLP to mitigate against some of the major risks like data loss, leakage, exfiltration, and breaches. These are significant concerns that we must address to protect sensitive information effectively:
3.1. Data Loss and Leakage
Data loss occurs when we can no longer access or use important data due to incidents like accidental deletion, system crashes, or hardware failure. For example, if we accidentally delete a file without a backup.
Data loss can also result from cyberattacks like ransomware, where attackers encrypt our data, making it unusable. This disrupts operations and could cause long-term damage to our business. DLP helps us mitigate this risk by enforcing backup protocols and securing data storage systems.
Data leakage refers to unauthorized or accidental exposure of sensitive information to external parties. It often happens unintentionally, for example, when we send a confidential document to the wrong email address or use unsecured cloud services.
In some cases, insiders may unintentionally or deliberately leak critical information, causing it to fall into the wrong hands. DLP solutions help us prevent this by monitoring data transfers, emails, and file-sharing activities to ensure sensitive data doesn’t leave our control without proper authorization.
3.2. Data Exfiltration and Data Breach
Data exfiltration is a malicious and targeted act of transferring sensitive data from an organization without permission. Cybercriminals or malicious insiders often execute exfiltration through hacking, phishing, or other sophisticated attacks.
Unlike accidental data leakage, data exfiltration involves deliberate efforts to extract valuable information, such as customer records or financial data.
Finally, data breaches represent a broad category encompassing data leakage and exfiltration. A breach occurs when unauthorized individuals gain access to sensitive information. For example, it can happen through vulnerabilities like weak passwords, phishing attacks, or existing security gaps in our systems.
Data breaches often lead to severe financial, legal, and reputational consequences. DLP helps us monitor, detect, and respond to violations immediately. It reduces the potential impact and ensures we meet regulatory requirements for breach notification.
By addressing data loss, leakage, exfiltration, and breaches with DLP strategies, we create a robust framework that protects our sensitive data, ensures compliance, and minimizes the risk of information falling into the wrong hands. DLP detects and blocks unauthorized attempts to transfer data outside the organization, allowing us to respond quickly and prevent large-scale data theft.
4. Adoption and Best Practices
We need to consider several factors before adopting a DLP solution. For example, DLP is not just about technology; it involves policies, processes, and people working together to secure sensitive information. With this kind of variation, we should ensure our policies don’t conflict.
As a result, let’s look at some of the factors we need to consider before and during adoption. Also, we’ll mention some of the best practices we can use:
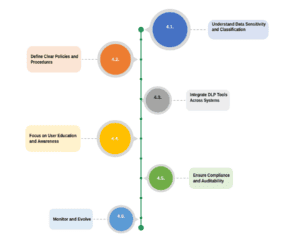
4.1. Understand Data Sensitivity and Classification
First, we need to identify and classify the kind of data we handle. Not all data requires the same level of protection. Personal information, financial records, and customer data all carry different risks. By categorizing data based on sensitivity, we can apply tailored DLP policies, ensuring we focus our efforts where they are most needed. Regularly updating this classification will help us adapt to changing business and regulatory requirements.
4.2. Define Clear Policies and Procedures
For DLP to be effective, we must create clear, enforceable policies that align with legal and regulatory obligations. These policies should define how we handle data, who can access it, and under what circumstances it can be shared or transferred.
Also, it should precisely define the procedures for managing incidents like data breaches or unauthorized access attempts. Hence, it ensures a swift and coordinated response.
4.3. Integrate DLP Tools Across Systems
To ensure that our DLP solution integrates seamlessly across all critical systems e.g., on-premises, in the cloud, or across endpoints like laptops and mobile devices. DLP tools should monitor data at rest, in motion, and in use, ensuring comprehensive coverage. Also, to strengthen our data security framework, we should integrate it with existing security systems, such as firewalls, encryption services, cloud security, and endpoint protection.
4.4. Focus on User Education and Awareness
Human error is one of the leading causes of data breaches and leaks. To mitigate this, we need to prioritize training our employees on data security best practices, including identifying phishing attacks, handling sensitive data, and following company policies. Regular training and awareness campaigns will help reduce mistakes and improve our security.
4.5. Ensure Compliance and Auditability
Our DLP strategy must meet regulatory compliance requirements, such as GDPR or industry-specific standards like PCI-DSS. We should regularly conduct audits and reviews to ensure we remain compliant. Furthermore, we should leverage DLP reporting tools to track incidents, data usage, and access attempts. This helps identify areas for improvement.
4.6. Monitor and Evolve
DLP is not a one-time solution. We must continuously monitor its effectiveness by analyzing the results, refining policies, and updating technologies. As new threats emerge and our business evolves, our DLP strategies should be flexible enough to adapt. We should regularly review our policies and tools to ensure they remain effective.
Considering these factors, we can create a robust DLP implementation that protects our data and aligns with business goals and regulatory standards.
5. Conclusion
In this article, we’ve looked at Data Loss Prevention and discussed what it is and the risks it intends to protect us from. Further, we looked at factors we should consider before adoption and the best practices to implement. DLP is a critical component of modern cybersecurity. With the increasing volume and sensitivity of data being stored and transferred digitally, organizations must implement robust DLP strategies to protect themselves from internal and external threats.