1. Overview
When we create passwords, applications must keep them secure to prevent unauthorized access. Hashing transforms a password into a fixed-length string that is nearly impossible to reverse. However, in many situations, hashing a password once is insufficient to provide total security.
Attackers use advanced methods like brute force attempts to crack hashed passwords. To prevent these risks, security experts recommend hashing passwords multiple times to prevent attackers from breaking them.
In this tutorial, we’ll look at why we should hash passwords multiple times.
2. Disadvantages of Single Hashing
Attackers have developed sophisticated methods for cracking hashed passwords, leveraging powerful technology and pre-computed data.
2.1. Brute Force Attacks
In a brute force attack, an attacker attempts every possible combination until they find one that matches the hashed password.
A hashed password can be identified using sufficient computational power, especially when the latest GPUs are used. Hashing once isn’t enough to keep attackers from checking millions of password combinations per second.
2.2. Rainbow Tables
Rainbow tables are pre-computed tables containing commonly used passwords and related hash values.
These tables enable attackers to find the original password by searching for its hash. Single-hash techniques, especially without safeguards like salts or repetitions, are vulnerable to rainbow table attacks.
2.3. Weak or Reused Passwords
Some people frequently reuse weak or common passwords.
If an attacker knows that many users often use passwords like qwerty, the attacker can hash it once and search for matches among all users.
2.4. Absence of Built-in Delays
Hashing a password only once takes less than a millisecond. This is helpful for authorized users but creates a significant weakness while under attack. Attackers can do millions of hash computations per second.
3. Key Considerations in Iterative Hashing
When we hash passwords multiple times, we make them much more secure:
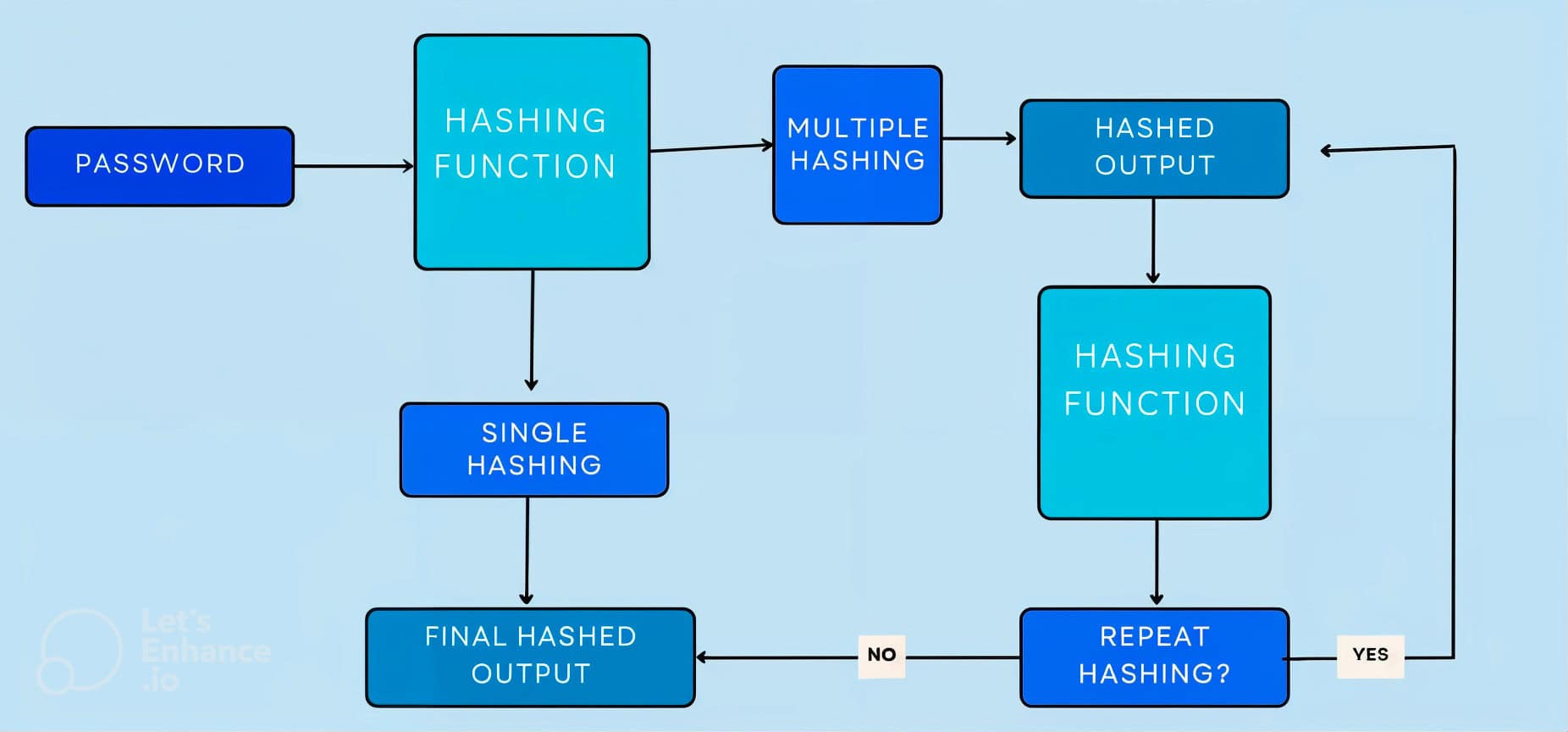
This process is commonly known as iterative hashing or key stretching. This strategy has several advantages.
3.1. Iterative Hashing Method
Iterative hashing involves hashing a password several times rather than once, making it more difficult for attackers to crack the hash.
Each iteration of the hashing process uses the previous hash’s output as input for the following round:
hashed_password = password
for i in range(1, number_of_iterations):
hashed_password = hash(hashed_password)
This increases the time required to generate the final hash, making it more difficult for attackers to brute-force or guess the password.
3.2. Recommended Number of Hashing Iterations
The number of iterations can vary depending on security requirements.
Common practice recommends 1,000 to 10,000 iterations, although algorithms such as bcrypt allow even more iterations to keep up with technological developments.
3.3. How Many Times Do We Hash?
Choosing the number of hashing iterations requires balancing security and performance. More iterations improve security by making it more difficult for attackers to hack our passwords; however, they may slow down the login process.
A decent starting point would be around 10,000 iterations, however this can be modified based on our system’s security requirements and hardware capabilities.
3.4. Do We Always Apply the Same Hashing Algorithm?
Using the same hashing algorithm in each iteration simplifies implementation. Although this method is more common, if the underlying hashing algorithm has vulnerabilities, an attacker could exploit them.
On the other hand, using different hashing algorithms in each iteration increases security. However, this adds complexity, as it requires careful coordination to ensure that all hash functions work together smoothly and are properly managed.
3.5. Salting and Peppering
To improve security, a unique salt, which is a random string of characters, is often added before hashing the password.
Salting ensures that even if two users share the same password, their hashes differ, thus preventing attackers from effectively exploiting pre-computed tables such as rainbow tables.
Another technique is peppering, which involves adding a secret key to the password before hashing it. This adds another layer of security, making it more difficult for attackers to crack the password even if they have the salt.
4. Why Does Iterative Hashing Work?
Iterative hashing increases the computational effort necessary for brute-force attacks, protects against rainbow tables, and adapts to changing hardware threats.
4.1. Increased Computational Costs
With a single round of hashing, attackers can test millions of randomly generated passwords per second using brute-force attacks or specialized hardware such as GPUs.
However, when we hash our passwords multiple times, the time required to break a password increases, making it much more difficult for hackers to figure out the password.
Furthermore, algorithms like bcrypt enable us to increase the number of iterations as hardware grows more powerful.
4.2. Defending Against Rainbow Tables
Introducing many rounds of hashing greatly complicates matters for a rainbow attack.
Iterative hashing increases the chance of producing a fully unique password-hash combination. Consequently, it makes it less likely for the password-hash pair to be in a rainbow table.
4.3. Adaptability to Future Threats
Password hashing techniques that hash only once can quickly become vulnerable to improved hardware with increased computational power. To address this issue, algorithms that support multiple rounds of hashing provide adaptability by allowing us to change the number of iterations over time.
The number of iterations, or hashing rounds, determines how many times the hashing algorithm is applied to the password. We can utilize algorithms such as bcrypt, PBKDF2, and others.
As hardware evolves, we can add extra hashing rounds to keep passwords secure without forcing users to update them. This adaptability future-proofs the system, ensuring it can grow to meet new threats.
5. Conclusion
In this article, we learned about how iterative hashing improves password security significantly by increasing computing costs, protecting against rainbow tables, and providing adaptation to new threats.
As attackers improve their strategies, implementing many rounds of hashing makes even weak passwords much more difficult to hack, ensuring strong security in the face of emerging threats.