1. Introduction
In modern networking, Virtual Local Area Networks (VLANs) play a crucial role in segmenting networks to improve performance, enhance security, and simplify management. With the growing demand for reliable and organized network infrastructure, VLANs have become essential for optimizing and securing organizational communication.
However, a common confusion arises when devices are on different VLANs but share the same IP subnet: they can’t communicate with each other.
In this tutorial, we’ll explore why this occurs by covering VLAN operation, subnetting principles, and the interaction between Layer 2 and Layer 3 networking. By understanding these aspects, we’ll gain insight into effective VLAN and subnet configurations that enhance network functionality and security.
2. Understanding VLANs
2.1. What Is a VLAN?
A Virtual Local Area Network (VLAN) is a logical grouping of network devices that allows devices to appear on the same LAN regardless of physical location. VLANs operate at the OSI model’s Data Link Layer (Layer 2).
By segmenting a network into VLANs, administrators can:
- reduce broadcast domains by limiting the scope of broadcast traffic
- enhance security by isolating sensitive devices from the rest of the network
- improve performance by reducing unnecessary traffic on the network
2.2. How Do VLANs Work?
In a VLAN-enabled network, switches assign ports to specific VLANs. Traffic between devices on the same VLAN is switched normally, while communication between different VLANs requires a Layer 3 device (e.g., a router).
Let’s explore a sample scenario:
- VLAN 10: assigned to ports connected to the Sales department
- VLAN 20: assigned to ports connected to the Engineering department
Devices on VLAN 10 cannot communicate with devices on VLAN 20 without routing.
You can check our introduction to VLAN for a more detailed tutorial on VLANs and their principles.
3. Understanding Subnets
3.1. What’s a Subnet?
A subnet is a logical subdivision of an IP network. Subnetting divides a network into smaller networks to manage traffic and improve security. They consist of:
- IP Addressing: devices within the same subnet share a common network address
- Subnet Mask: determines the network and host portions of an IP address
3.2. How Do Subnets Work?
Subnets operate at the OSI model’s Network Layer (Layer 3). Routers use IP addresses to direct traffic between subnets.
Let’s see an example scenario for subnets as well:
- Subnet 192.168.1.0/24: devices with IP addresses from 192.168.1.1 to 192.168.1.254
- Subnet 192.168.2.0/24: devices with IP addresses from 192.168.2.1 to 192.168.2.254
Devices in different subnets require routing to communicate. For more detailed information about subnets and their work, refer to our detailed tutorial on Subnets in IPv4 Networks.
4. Comparing VLANs and Subnets
To understand why devices on different VLANs but the same subnet cannot communicate, we should compare VLANs and subnets in terms of their functions and operations:
Aspect
VLAN
Subnet
OSI Layer
Data Link Layer (Layer 2)
Network Layer (Layer 3)
Purpose
Segments network at Layer 2 to reduce broadcast domains and enhance security
Divides IP address space at Layer 3 to manage network traffic and address allocation
Identification
VLAN ID (typically a number between 1 and 4094)
Network address and subnet mask (e.g., 192.168.1.0/24)
Communication Within
Devices in the same VLAN can communicate directly at Layer 2
Devices in the same subnet can communicate directly at Layer 3
Communication Between
Requires Layer 3 routing to communicate between VLANs
Requires routing to communicate between different subnets
Configuration
Configured on switches by assigning ports to VLANs
Configured via IP addressing and subnet masks on devices and routers
Isolation
Provides Layer 2 isolation; devices in different VLANs are in separate broadcast domains
Doesn’t inherently provide isolation; devices in different subnets can be on the same physical network unless VLANs are used
While VLANs and subnets both serve to organize and manage network traffic, VLANs segment the network at Layer 2 to isolate broadcast domains. In contrast, subnets operate at Layer 3, dividing IP address spaces for traffic management.
Therefore, even if devices share the same subnet, they cannot communicate across VLANs without routing, as each VLAN isolates network traffic at the data link layer.
5. The Issue: Devices on Different VLANs but Same Subnet
Let’s consider a scenario where two devices are assigned IP addresses in the same subnet but are placed on different VLANs:
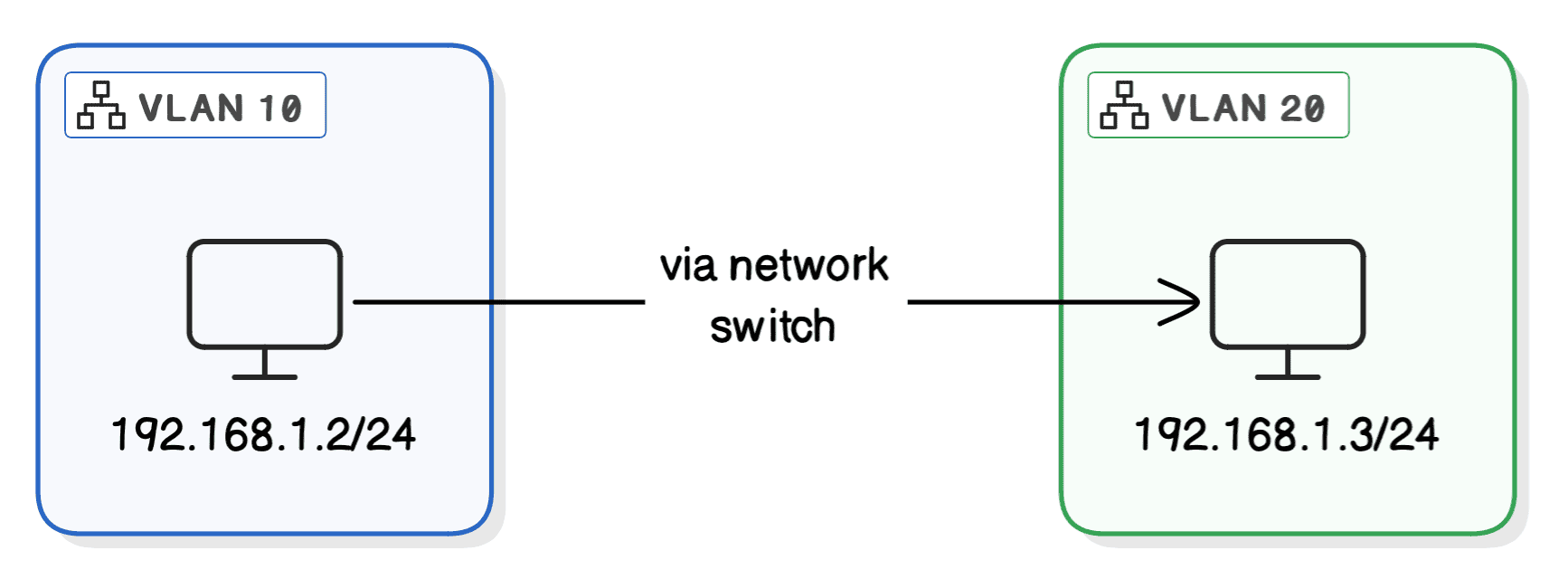
Despite being on the same IP subnet, Device A and Device B cannot communicate with each other. This occurs because VLANs create separate broadcast domains, and devices rely on broadcasts like ARP requests to communicate within the same subnet.
5.1. Layer 2 Broadcast Domains
VLANs confine broadcast traffic to their own domains.
When Device A attempts to communicate with Device B, it sends an ARP request to resolve the MAC address associated with 192.168.1.3.
Since broadcasts are limited to VLAN 10, Device B on VLAN 20 never receives this request. As a result, Device A cannot discover Device B’s MAC address or establish communication.
5.2. Absence of Layer 3 Routing
Devices determine whether to send packets directly or via a router based on the destination IP address and subnet mask.
Since both devices are in the same subnet, they assume direct Layer 2 communication is possible and do not attempt to route the traffic through a Layer 3 device.
However, the VLAN separation at Layer 2 blocks this direct communication, leading to a failure in connectivity.
6. Solution: Implement Inter-VLAN Routing
One solution we can introduce is a Layer 3 device capable of routing between VLANs. It allows devices to communicate across VLANs, even within the same subnet. We can do it in two ways.
6.1. Using a Router
A router can be configured with subinterfaces, each associated with a VLAN. This setup is known as “Router-on-a-Stick”:
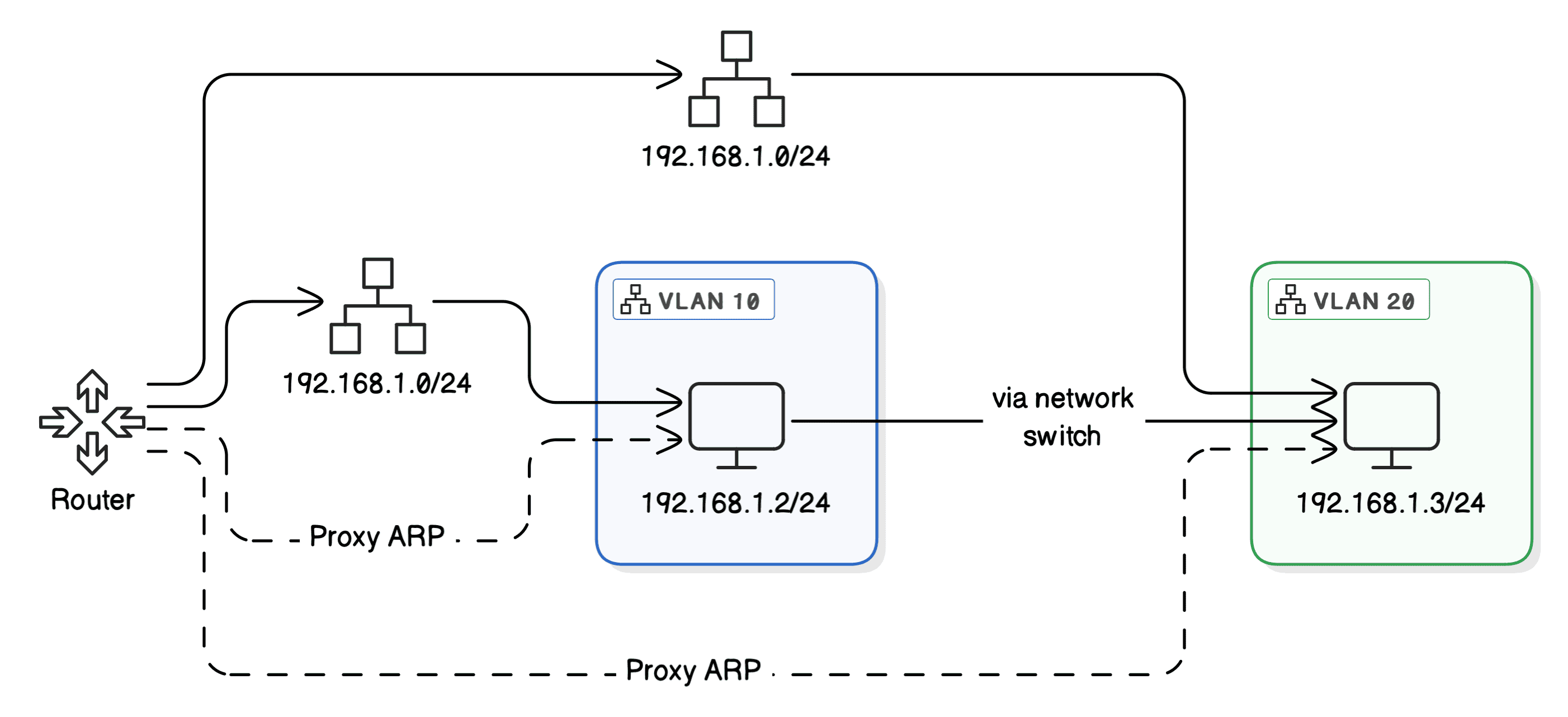
To set up VLANs on our router, we create a subinterface for each VLAN. Next, we assign the same subnet to both subinterfaces, allowing devices in both VLANs to communicate within the same IP range. Finally, we enable Proxy ARP on the router so it can respond to ARP requests on behalf of devices in other VLANs. This setup ensures smooth cross-VLAN communication.
While enabling Proxy ARP can facilitate communication, we should note that it also introduces potential security risks by allowing inter-VLAN communication without restriction.
6.2. Using a Layer 3 Switch
Another option is to use a Layer 3 switch to combine switching and routing capabilities, allowing for efficient inter-VLAN routing:
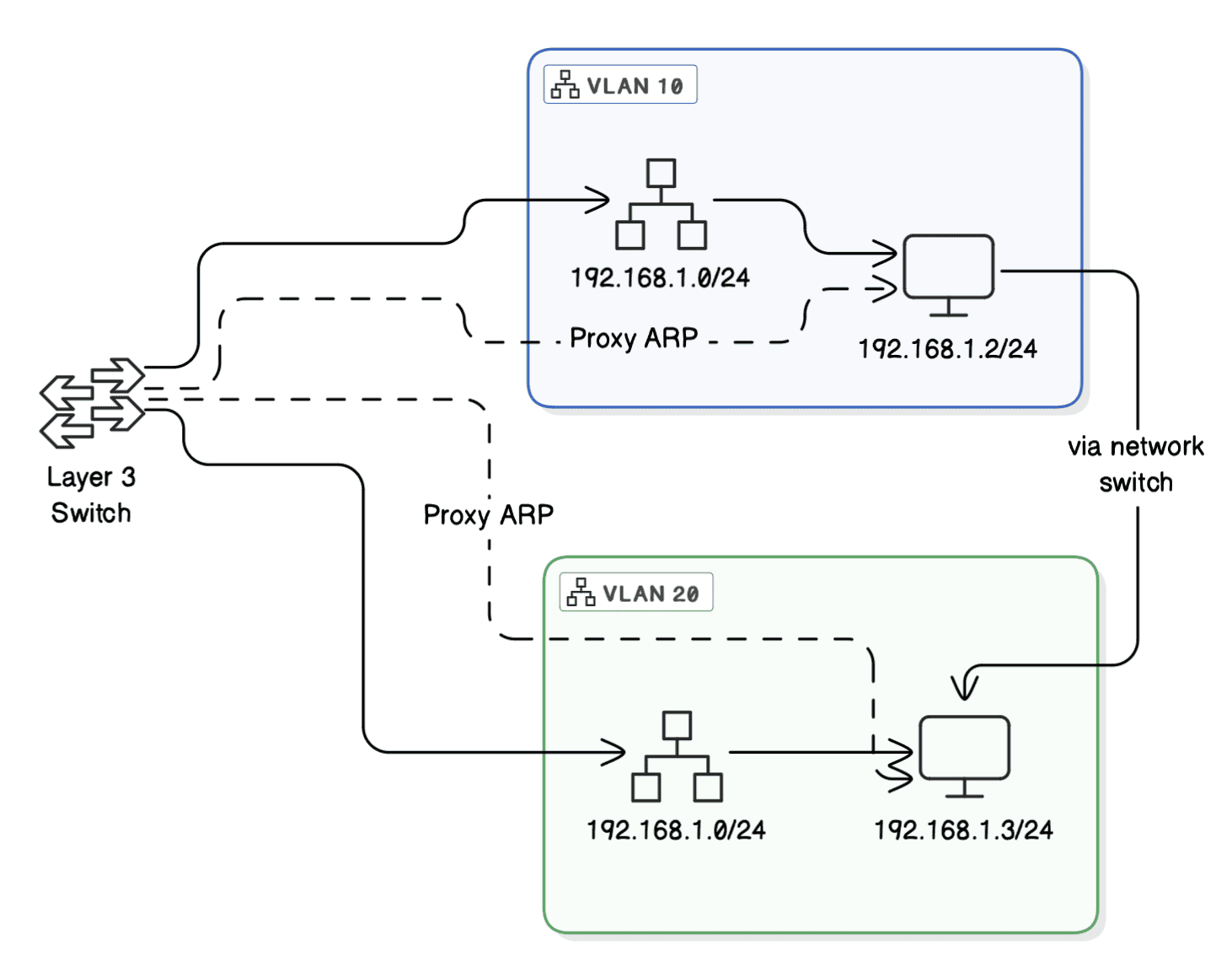
To configure our network, we start by setting up Switch Virtual Interfaces (SVIs) for each VLAN. Then, we assign IP addresses to each SVI within the same subnet, allowing devices across VLANs to communicate smoothly. We also enable inter-VLAN routing and Proxy ARP to support seamless interaction between VLANs if needed.
7. Solution: Reassign Subnets to VLANs
Assigning different subnets to each VLAN and adding Internet Gateway is a more common and recommended practice:
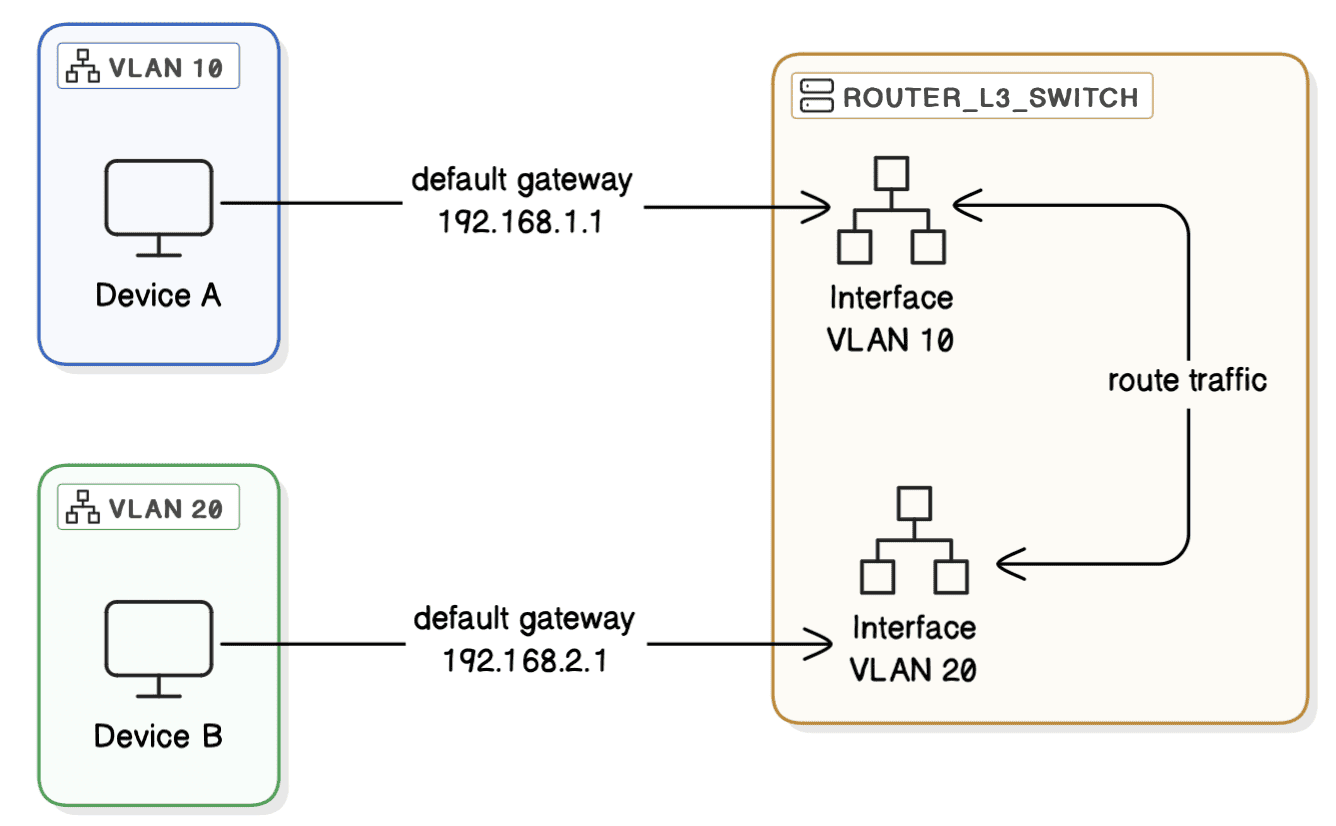
First, we assign unique subnets to each VLAN to ensure clear network segmentation. For example, we use 192.168.1.1/24 for VLAN 10 and 192.168.2.1/24 for VLAN 20. This setup helps devices identify destinations on different networks, directing traffic to the default gateway for routing.
Next, we configure default gateways by setting each device’s gateway to the IP address of the router or Layer 3 switch interface within its VLAN. This enables efficient routing and communication within the network.
We enable inter-VLAN routing on the router or Layer 3 switch to support communication between VLANs. This configuration allows traffic to pass smoothly between the different subnets assigned to each VLAN.
This approach has several benefits. It aligns our network with standard practices through proper Layer 3 segmentation, simplifies routing for easier configuration and troubleshooting, and enhances security by reducing unwanted communication between VLANs.
8. Conclusion
In this article, we discussed why devices on different VLANs within the same subnet cannot communicate.
The main reason is that VLANs isolate Layer 2 broadcast domains, preventing necessary protocols like ARP from resolving MAC addresses across VLANs.
Without proper routing, devices assume they can communicate directly (since they are in the same subnet) but are blocked by VLAN segmentation.